Understanding Concept of ACL’s
IP ACL (IP Access Control Lists), they perform various functions on Cisco routers packet filter being its main function. ACL is also used to match packets for applying QoS(Quality of Service).
For examples, if we have two kind of packets such as voice packets and data packets. The ACL’s match voice packets and by using QoS logic it prioritizes voice packets over data packets.
ACL Location and Direction:

Observe the image above, the location of ACL with packets can be at inbound of router or at the outbound of the router i.e., ACL’s are independent of routing logic used by routers.
Let’s explain that in detail. The four dotted arrows represent the route taken by host B to reach server S1, if we want to filter the packets of host B then we have to enable ACL on the interface on the routing path i.e., F0/0(R1), S0/0/0(R1), S0/0/1(R2) and F0/0(R2).
Matching packets refers to how to configure the ACL commands to look at each packet, listing how to identify which packets should be discarded and which should be allowed through.
Specifically, the ACL looks for header fields you should already know well, including the source and destination IP addresses, plus TCP and UDP port numbers.

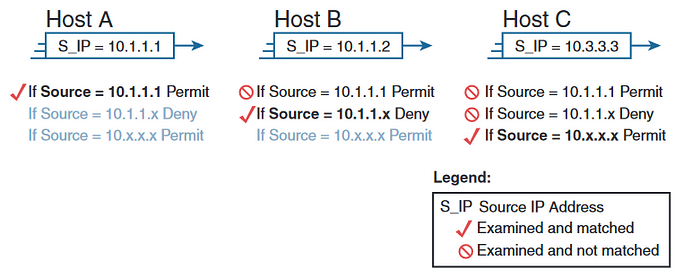
The above image speaks for itself, we have applied ACL logic at interface S0/0/1(R2) and the logic works by matching source address of the host B. If it matches then it filters the packets with the source ip.
The configuration commands use the keywords deny and permit, and they mean (respectively) to discard the packet or to allow it to keep going as if the ACL did not exist.
There are different types of ACL’s which can be classified as follows.
■ Standard numbered ACLs (1–99)
■ Extended numbered ACLs (100–199)
■ Additional ACL numbers (1300–1999 standard, 2000–2699 extended)
■ Named ACLs
■ Improved editing with sequence numbers
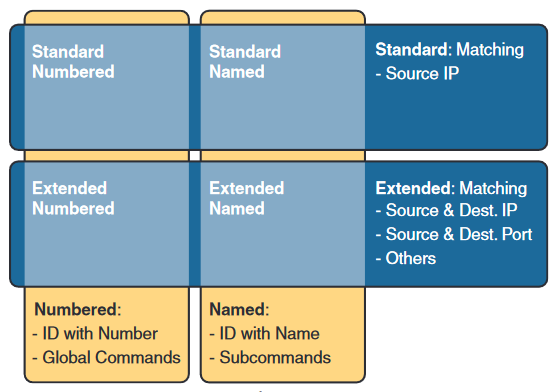
The above figure shows the core ideology of the ACL’s with the distinction between different types of ACL types and as well as ACL matching type.
When doing ACL processing, the router processes the packet, compared to the ACL, as follows:
ACLs use first-match logic. Once a packet matches one line in the ACL, the router takes the action listed in that line of the ACL and stops looking further in the ACL.

consider the above image, the ACL is applied at inbound interface of router R2 and the pseudo code used for ACL is shown in the table below and the logic used for ACL can be shown as below.
Matching logic and command syntax:
access-list {1–99 | 1300–1999} {permit | deny} matching-parameters
Each standard numbered ACL has one or more access-list commands with the same number, OS refers to each line in an ACL as an Access Control Entry (ACE), but many engineers just call them ACL statements.
To match exact ip address the command is as follows.
access-list 1 permit 10.1.1.1
In older version of IOS it is as follows
access-list 1 permit host 10.1.1.1
Matching a subset of the Addresses with wildcards:
If you want to filter a set of ip addresses then we can use tool called wildcard mask. This is not a subnet mask. The wildcard contains only two values either 0 or 255
Decimal 0: The router must compare this octet as normal.
Decimal 255: The router ignores this octet, considering it to already match.

So from the above figure, in the first one first three octets will be matched, in second one first 2 octets will be matched and in third one only first octet will be matched.
Now consider again the image as above and instead of using pseudo code we will use the actual commands that can be seen below.

Finding the right wild mask to match the subnet:
If we want to actually filter packets from entire subnet then the wild card corresponding to it can be found by using two statements as below.
■ Use the subnet number as the source value in the access-list command.
■ Use a wildcard mask found by subtracting the subnet mask from 255.255.255.255.
Let us consider a subnet 172.16.8.0 255.255.252.0 then the command for the implementing ACL is as follows.
access-list 1 permit 172.16.8.0 0.0.3.255
To match many or all addresses then we can use the following command
access-list 1 permit any
We can accumulate the all the information we learnt and concise them into following steps.
Generic syntax is as follows
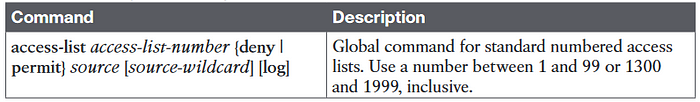
access-list access-list-number {deny | permit} source [source-wildcard]
Step 1. Plan the location (router and interface) and direction (in or out) on that interface:
A. Standard ACLs should be placed near to the destination of the packets so that
they do not unintentionally discard packets that should not be discarded.
B. Because standard ACLs can only match a packet’s source IP address, iden-
tify the source IP addresses of packets as they go in the direction that the
ACL is examining.
Step 2. Configure one or more access-list global configuration commands to create
the ACL, keeping the following in mind:
A. The list is searched sequentially, using first-match logic.
B. The default action, if a packet does not match any of the access-list commands, is to deny (discard) the packet.
Step 3. Enable the ACL on the chosen router interface, in the correct direction, using
the ip access-group number {in | out} interface subcommand.
Let’s consider the first example we considered above again. it’s configuration can be summarized as follows.


Command Reference sheet for ACL’s is as follows


Reference:
https://www.amazon.in/Exam-78-Official-Cert-Guide/dp/1587147130